Theory of operation
Traffic management on the X2-Series is done using rules and rule sets.
Rule sets are traffic management profiles created by the user. Multiple rule sets can be created, with one of them active at any given time.
A rule set consists of the following facilities:
- Traffic rules
- Traffic deduplication
- Load balancing groups
- Ingress rules
- Time synchronization
Rules define how the traffic will be processed by the packet broker. Only data matching at least one of the defined rules will pass through, everything else will be dropped.
X2-Series devices support up to 6000 “one port to one port” rules, or “interface links”. Each rule can contain one or more interface links. For optimizing rule utilization, see Optimizing rule consumption.
Traffic deduplication is used to detect and drop duplicate packets.
Load balancing groups are logic groups of ports that are used to distribute the traffic stream across multiple interfaces.
Ingress rules are used to manipulate traffic on the interface ingress pipeline.
Time synchronization can be set to connect to a PTPv2 server in order to perform high quality nanosecond precision traffic timestamping for ERSPAN type 3 encapsulated traffic.
Rules and rule sets are configured on the web GUI's Traffic Management page.
The Active tab displays the currently active rule set and its details, including the filtered interfaces, interfaces linked in load balancing groups, ingress rules, and time synchronization settings and status.
The Rule Sets tab displays the list of existing rule sets on the device. The active rule set is highlighted. Users with appropriate permissions can create, configure, activate, rename, delete, import, and export rule sets.
After clicking the configure button of a rule set, rules can be added, modified, or deleted.
After configuring a rule set, it can be activated right away, or kept inactive for future use. If changes have been made to the currently active rule set, it must be activated again for the changes to take effect.
Traffic deduplication
X2-Series NPBs are capable of performing traffic deduplication (license required). This feature is useful when the same packets are captured from different tapping points and aggregated in the packet broker.
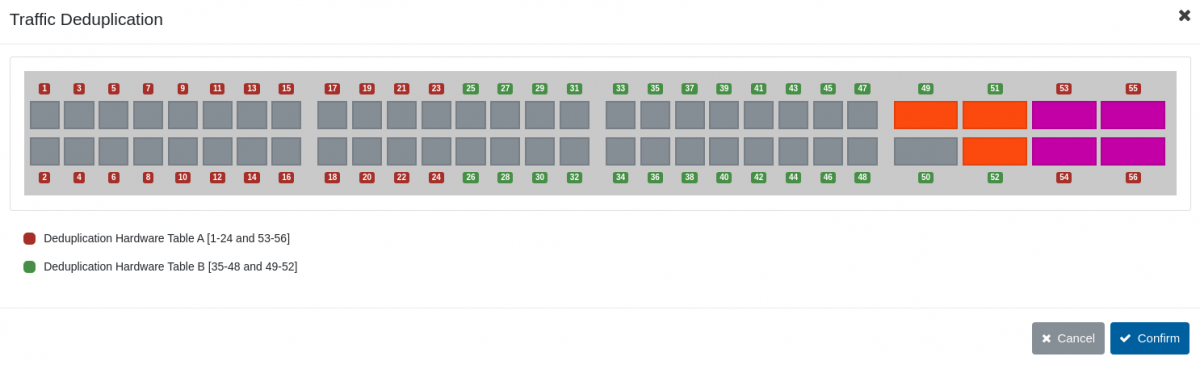
This feature can be controlled via the Configure Deduplication button in the traffic management view. Clicking this button opens a new view, allowing the user to select the interfaces on which the device will check for duplicate packets. The deduplication configuration view displays different colors for ports wired to the different hardware tables that the device is using to compare the incoming packets. Only traffic incoming on ports wired to the same hardware table (i.e. ports displayed with the same color) is evaluated for deduplication.
Note that the traffic identification will happen in the interface ingress, using the following fields:
- IPv4/6: Source and Destination Addresses;
- IPv4/6: Protocol/Next Header field;
- IPv4 Identification;
- TCP/UDP/SCTP: Source and Destination ports (or relative offset in fragmented traffic);
- TCP/UDP/SCTP: Checksum.
Load balancing groups
When a load balancing group is enabled for a group of interfaces, it is important to remember that when a port is inserted in one of these groups, it cannot be used in additional rules and will be displayed as unavailable in the port layout. Additionally, in order to have a consistent behavior of the load balancing group, all of the interfaces belonging to that group must operate at the same speed.
It is possible to change the traffic distribution strategy via the Configure button in the Load Balancing Group section of the Rule Set. In this view, it is possible to select between:
- Round Robin: Traffic will be distributed equally across all of the output ports;
- Flow Hash: Traffic will be distributed based on the selected headers fields.
Note that if Flow Hash is used with source AND destination options enabled for L3 or L4, the unit will make sure to distribute the traffic maintaining flow symmetry and consistency.
Ingress rules
On the X2-Series, users can define specific traffic manipulation rules to be performed on the interface ingress pipeline. Note that these operations will be performed before the filter and action engine described above. Users should ensure that the configured ingress rules don’t impact the functionality of the other rules.
Each Rule Set can include an independent set of ingress rules associated to each port. Note that it is only possible to have a single rule per port, and that these ports will only be available as input in other rules.
The available traffic manipulation options are:
- VLAN Tag: Adds a VLAN tag to all traffic incoming in the selected port;
- VLAN Strip: Removes a VLAN tag from all traffic incoming in the selected port;
- IPv4 Address: Allows the device interface to receive routed traffic in an IPv4 network;
- GRE-TAP Tunnel Stripping: All incoming GRE-TAP traffic will be automatically stripped of the external tunnel;
- GRE-TAP Tunnel Termination: When enabled, users can associate a MAC and IPv4 Address to the selected interface. This will be available in the network and can be used to direct a GRE-TAP (Ethernet over GRE) tunnel in the NPB interface. The traffic will be decapsulated and processed further using the other user rules;
- ERSPAN Tunnel Stripping: All incoming ERSPAN traffic will be automatically stripped of the external tunnel;
- ERSPAN Tunnel Termination: Terminates and decapsulates an ERSPAN tunnel directed to the configured IPv4 address;
- VXLAN Tunnel Stripping: All incoming VXLAN traffic will be automatically stripped of the external tunnel;
- VXLAN Tunnel Termination: Terminates and decapsulates a VXLAN tunnel directed to the configured IPv4 address and UDP port.
Time synchronization (X2-3200G, X2-6400G)
This section can be used to configure the Time Synchronization port. This interface only operates with 1G SFP modules.
The system works as a PTPv2 slave clock and will use the synchronized time to perform high quality nanosecond precision traffic timestamping for ERSPAN type 3 encapsulated traffic.
Click the Configure Time Synchronization button to configure the MAC and IP address associated with the port. Information about the internal synchronization process and its performance is then available from the Rule Set page's PTPv2 Time Synchronization table.
The System Synchronization State section provides information about the current state of synchronization. The possible states are:
- Inactive: Synchronization port is disabled;
- Freerun: Synchronization has not completed correctly and the system is timestamping with its own clock rate;
- Progress: System is synchronizing against a local master clock and is trying to rearrange its clock frequency to follow the master;
- Locked: System is synchronized against the local master clock and the timestamping clock has an average error within ±500 ns.
This view also provides information about the clock offset against the master clock and the time server's IP address.
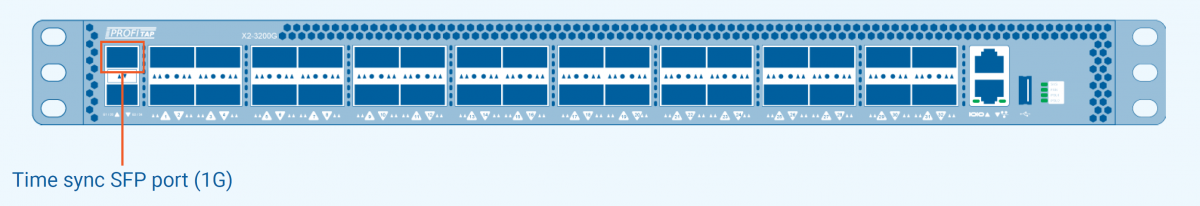
Time synchronization port on X2-3200G
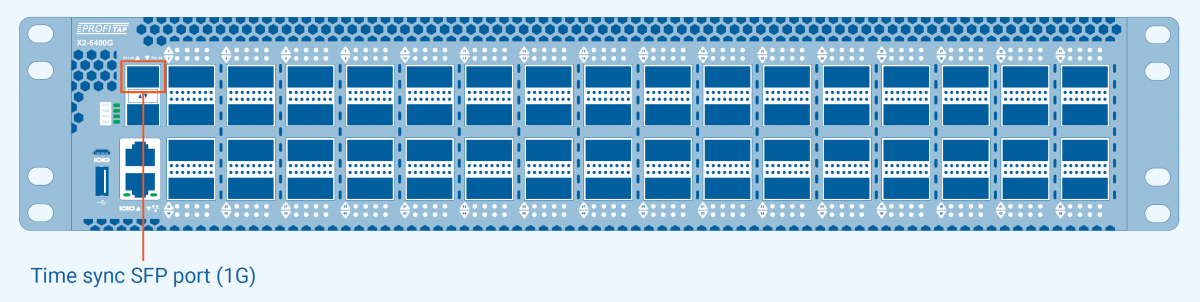
Time synchronization port on X2-6400G
Creating a rule

The first step in creating a new rule is defining the behavior of that rule [1]. The possible options are:
- Accept: Only traffic matching the defined filters will be forwarded;
- Drop: Traffic matching the defined filters will be removed from the stream.
The Input ports and Output ports sections [2] define which ports will be used as source for the traffic stream, and which ports will be used as destination.
⇒ When selecting multiple input ports, the traffic incoming on these interfaces will be aggregated (N:1 configuration).
⇒ When selecting multiple output ports, the traffic stream to these interfaces will be replicated (1:M configuration).
⇒ If multiple inputs and outputs are selected, the device will first aggregate the incoming traffic and then replicate the resulting stream to all of the selected output ports (N:M configuration).
If load balancing groups have been created, they appear in the Load Balancing Groups section [3]. Selecting one or more groups here will set them as output, in which case output interfaces won't need to be selected in the section above. Selecting multiple load balancing groups will replicate the traffic to each of these groups.
The Priority class option [4] can be used to create a filtering hierarchy. This feature can be used to define complex configurations, in which the user wants to create exception cases within drop or allow filters. The device supports six priority classes, which are processed from 5 (highest priority) to 0 (lowest priority). Note that, within the same priority class, rules dropping traffic always have the priority over rules allowing traffic.
The Enable counter option [5] can be enabled to start a counter monitoring the amount of packets matching the defined filter. These counters will be displayed in the Frame Match column of the Active tab's Rules table.
The Filters tab [6] allows the user to configure the way in which traffic is targeted, according to specific rules related to its L2, L3 and L4 packet headers:
- Ethernet Layer
Only frames matching MAC details configured in this section will be targeted (Source/Destination MAC Address, Source/Destination MAC Mask), with the possibility to select the packet type (IPv4, IPv6, ARP, TCP (IPv4/6), UDP (IPv4/6), SCTP (IPv4/6), Custom Protocol (IPv4/6), or any). - IPv4/IPv6 Layer
When IPv4/IPv6 is selected, the board will filter for any packet of those types. In order to filter for the IPv4/IPv6 details, the user needs to fill in the related fields (Source/Destination IP Address, Source/Destination IP Mask). The Protocol Type setting is only configurable for IPv4/IPv6, allowing the user to restrict the traffic to a specific type of L4 header (TCP, UDP, SCTP, ICMP, IGMP). Any allows filtering a custom EtherType or setting no filter for L3 headers. IPv6 Source and Destination Addresses filtering is only possible if the Rule Set is configured with IPv6 Addresses Filtering (Configure Filtering button on the Rule Set page). - TCP/UDP/SCTP Layer
When TCP/UDP/SCTP is selected in Protocol Type, only packets matching the transport layer details configured in this section will be filtered. This can be done by clicking the L4 Ports Group Edit button, creating a group, naming it, and deciding how the port group will appear, by listing the exact ports followed by comma, or by selecting a range of allowed ports. After creating the group, the desired filter needs to be selected by typing/selecting the group name in the Source/Destination Ports Groups subsection. - VLAN Tags
Can be used for filtering as outer/inner VLAN. This can be done by clicking the VLAN ID Group Configuration button, creating a group, naming it, and deciding how the port group will appear, by listing the exact ports followed by comma, or by selecting a range of ports. After creating the group, in order to be activated, the desired filter needs to be selected by typing the group name in the Outer/Inner VLAN ID subsection. The selections cannot overlap. - MPLS Labels
This section can be used to filter on MPLS labels. Up to six MPLS labels can be specified. Note that each label will match only with the one in the specified position. This option is only available if the Rule Set is configured with MPLS Filtering enabled (Configure Filtering button on the Rule Set page).
Note: If multiple filter fields are configured, only packets matching all filters will be targeted.
The Advanced tab [7] allows the configuration of options that can be applied to the traffic in outbound, as well as advanced filtering:
- Strip VLAN Tag/Add VLAN Tag
A VLAN header with the specified VLAN ID can be added. The new tag is always added externally. Packet EtherType fields are guaranteed to be updated automatically. If VLAN Strip is enabled, the outer VLAN tag is removed. If both options are enabled at the same time, the external VLAN ID tag will be replaced by the one specified. - Strip MPLS Tag
Remove either the outer MPLS label or all MPLS labels in all packets passing through the rule. - Slicing
Truncates the packets to the specified size (between 64 and 9215 bytes). - MAC Address Spoofing
This function allows the source and/or destination MAC addresses to be replaced with the specified ones. - Tunnel Filter
Filter traffic encapsulated in the following tunneling protocols:- Inner IPv4: Filter traffic based on inner IPv4 encapsulated in the following tunneling protocols: IP in IP, GTP, GRE L3.
- VXLAN: Filter VXLAN traffic based on VNI value. Use “VNI mask (hex)” for bulk VNI values.
- ERSPAN: Filter ERSPAN traffic based on Session ID. Use “Session ID mask (hex)” for bulk session IDs.
- Tunnels Stripping
Allows the user to remove tunnel headers for the following protocols:- IP in IP;
- GRE-TAP;
- ERSPAN;
- VXLAN;
- Teredo.
- Traffic Tunneling
Encapsulate the traffic passing through the rule in an ERSPAN type 2, ERSPAN type 3, or GRE tunnel. The address fields and optionally the tunnel VLAN used in the tunnel must be specified. If ERSPAN type 3 tunnel is selected, the packets will also include a nanosecond precision timestamp. It is also possible to truncate the tunneled traffic by specifying the maximum size for each packet in bytes.