Accessing IOTA & network configuration
Note: This article is deprecated. For the up-to-date versions of this article, see kb.profitap.com/iota/
Accessing IOTA over the network
To access the IOTA over the network, connect to the HTTPS interface by browsing to the device IP of your IOTA.
The full URL should be: https://<ip_addr>
DHCP mode is enabled by default. If no IP is assigned to the IOTA, the default fallback IP is 169.254.1.1.
To login, use the following initial credentials:
- Default username: admin
- Default password: admin
Note: Make sure to change the default credentials as soon as possible.
IOTA 10 CORE
On IOTA 10 CORE, connect management port M1 to the network used to access the unit. The management interface will attempt to get an IP address from a DHCP server. If it is unable to get an IP address over DHCP, the default fallback IP is 169.254.1.1 with netmask 255.255.0.0.
Network settings can be modified via the IOTA GUI (see Network configuration) or by using the unit's USB ports (see Network configuration via USB).
Network configuration
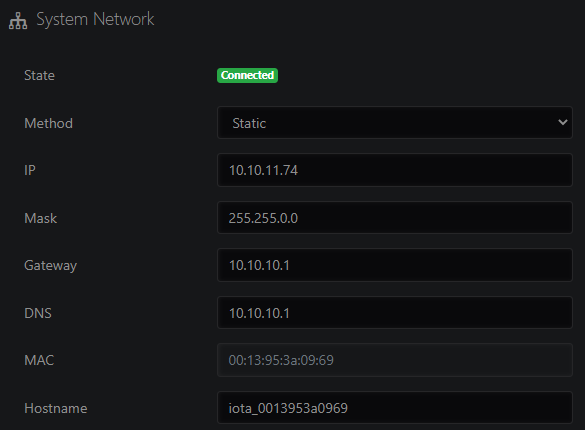
Navigate to IOTA Settings > Network Configuration to modify the IOTA network settings. The IP address, network mask, gateway and DNS server can be set manually if Method is set to Static. If Method is set to DHCP Dynamic, IOTA will attempt to receive network settings from a DHCP server.
Access / internal firewall
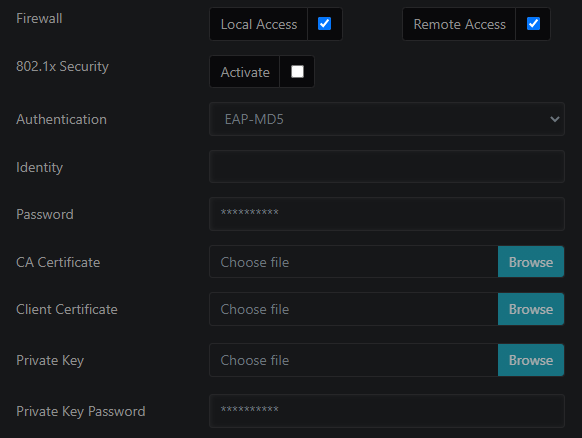
Firewall
Local Access
When enabled, connections to the IOTA user interface from the subnetwork IOTA is located on are accepted. When disabled, they are rejected.
Remote Access
When enabled, connections to the IOTA user interface from subnetworks other than the one IOTA is located on are accepted. When disabled, they are rejected.
802.1x Security
Activate
Enable or disable 802.1x authentication.
Authentication
Defines the authentication method:
- 'EAP-MD5': The EAP-MD5 (message-digest algorithm v5) method checks against the MD5 hash of the user password for authentication. The EAP-MD5 is defined in RFC 2284.
- 'EAP-TLS': The EAP-TLS (Transport Layer Security) uses Public key Infrastructure (PKI) to set up authentication using a RADIUS or other authentication server. This protocol requires client-side certificates for communicating with the authentication server. The EAP-TLS is defined in RFC 5216.
Identity
Specifies the username for the 802.1x EAP-MD5 or EAP-TLS server.
Password
Specifies the password for the 802.1x EAP-MD5 server.
CA Certificate
The CA certificate file (Certificate Authority) in PEM format for the 802.1x EAP-TLS server (optional).
Client Certificate
The client certificate file in PEM format for the 802.1x EAP-TLS server.
Private Key
The private key certificate file in PEM format for the 802.1x EAP-TLS server.
Private Key Password
Specifies the password for the private key file for the 802.1x EAP-TLS server (optional).
ZeroTier
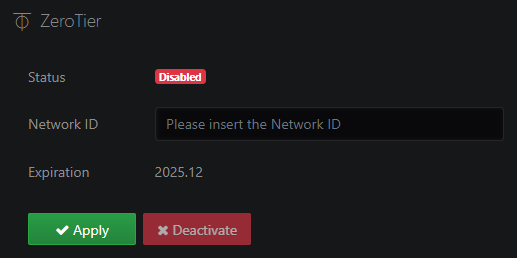
ZeroTier provides an easy way to remotely access the device via a P2P VPN and manage virtual networks on a cloud application. See ZeroTier configuration for more information.
Note: The ZeroTier access is a licensed feature. The Expiration section shows the service expiration date of the current ZeroTier License.
Network configuration via USB
Applies to: IOTA 10 CORE
To modify network settings via USB, create a file called iota_networking.json, place this file at the root of a USB drive, connect the USB drive to one of the unit's USB ports, and power on or restart the unit.
The iota_networking.json file should contain the desired network configuration. For instance, to set a static IP, use the following JSON content:
{
"dhcp_enabled": false,
"ip": "192.168.1.9",
"netmask": "255.255.255.0",
"gateway": "192.168.1.1",
"nameserver": "192.168.1.1"
}
Replace the information above with the desired network settings.
The possible network settings are as follows:
"dhcp_enabled": [true/false]
If set to “true”, the device will attempt to get network settings from a DHCP server. Values for “ip”, “netmask”, “gateway” and “nameserver” are ignored in this case.
If set to “false”, the device will not attempt to get network settings from a DHCP server. Values for “ip”, “netmask”, “gateway” and “nameserver” must be specified in this case.
"ip": "[IPv4 address]"
Sets a static IPv4 address if “dhcp_enabled” is set to “false”.
"netmask": "[IPv4 netmask]"
Sets a static IPv4 subnet mask if “dhcp_enabled” is set to “false”.
"gateway": "[IPv4 gateway]"
Sets a static IPv4 gateway if “dhcp_enabled” is set to “false”.
"nameserver": "[IPv4 DNS]"
Sets a static IPv4 DNS if “dhcp_enabled” is set to “false”.
"hostname": "[string]"
Changes the device's hostname.
"allow_internal_access": [true/false]
If set to “true”, connections to the IOTA user interface from the subnetwork IOTA is located on are accepted. If set to “false”, they are rejected.
"allow_external_access": [true/false]
If set to “true”, connections to the IOTA user interface from subnetworks other than the one IOTA is located on are accepted. If set to “false”, they are rejected.
"network_authentication_enabled": [true/false]
Enables or disables 802.1x authentication. If enabled, one and only one of the authentication methods' (MD5 or TLS) settings must be specified, as shown below.
802.1x EAP-MD5:
"network_authentication_md5":
{
"identity": "foobar",
"password": "barfoo"
}
802.1x EAP-TLS:
"network_authentication_tls":
{
"identity": "foobar",
"ca_cert": "foobar",
"client_cert": "foobar",
"private_key": "foobar",
"private_key_pw": "foobar"
}
Example of a complete iota_networking.json file:
{
"dhcp_enabled": false,
"ip": "192.168.1.9",
"netmask": "255.255.255.0",
"gateway": "192.168.1.1",
"nameserver": "192.168.1.1",
"hostname": "profitap-iota",
"allow_internal_access": true,
"allow_external_access": true,
"network_authentication_enabled": true,
"network_authentication_tls":
{
"identity": "foobar",
"ca_cert": "foobar",
"client_cert": "foobar",
"private_key": "foobar",
"private_key_pw": "foobar"
}
}