Security monitoring in high throughput environments
The Challenge
Enterprises often fail to pay close attention to what goes on before a cyber attack. Many assume that a single Network Security Monitoring (NSM) tool or the occasional test is sufficient to prevent, detect and respond to attacks which are so common today. However, just collecting and analyzing data doesn’t get you there. Malicious activity often masquerades as legitimate activity. This means your organization requires continuous monitoring, with a diverse toolset.
While some of these requirements can be fulfilled by accessing network data through SPAN/mirror ports on switches in low bandwidth environments, multi-gigabit per second environments require a dedicated solution to access, manage, and analyze the traffic.
The joint solution of Security Onion and Profitap offers the most efficient end-to-end monitoring platform you can get for highspeed networks. It offers reliable access to the network and actionable data for the visibility you need to identify on anomalous events.
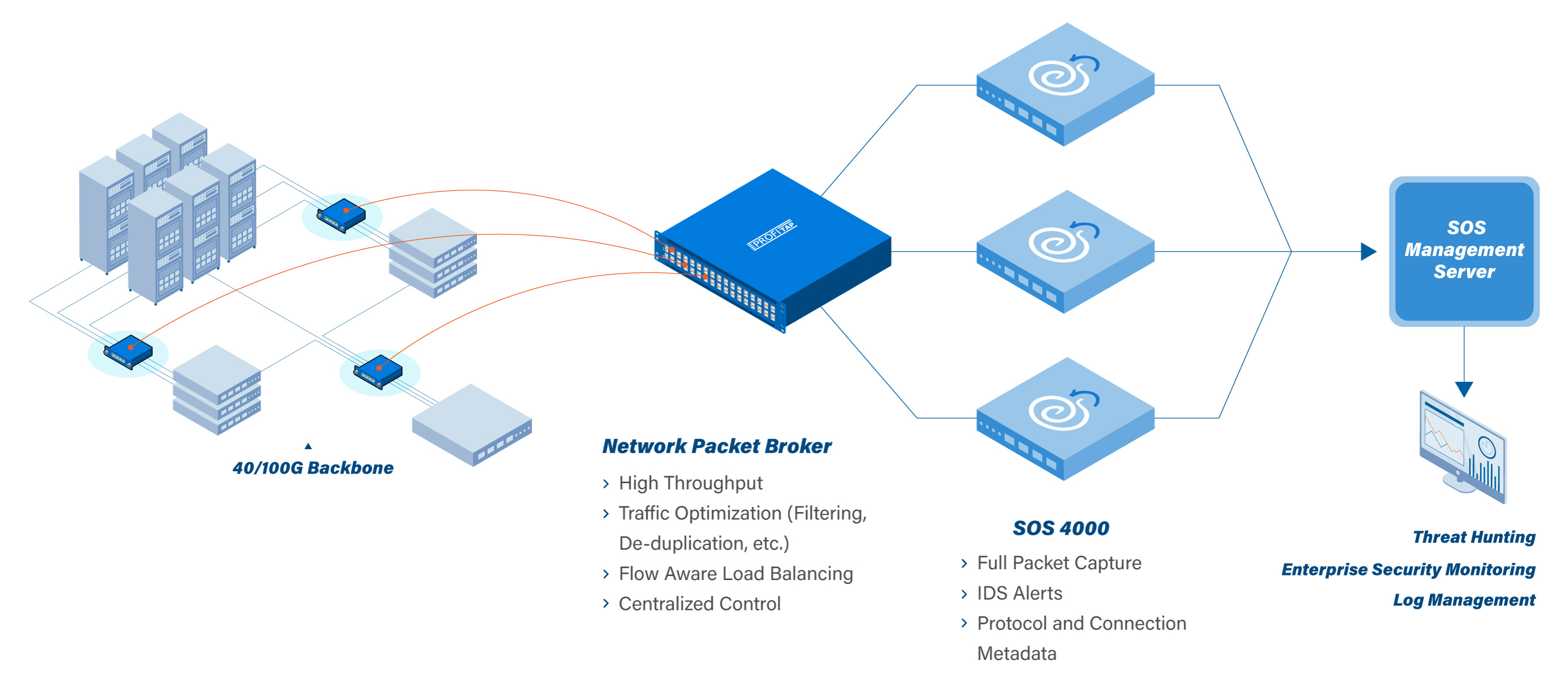
Security Onion provides a suite of tools, including full packet capture, network-based and host-based intrusion detection systems, and network and protocol metadata collection, combined with powerful analysis tools used to slice and dice network, endpoint, and application log data.
Profitap’s innovative Network TAPs and Packet Brokers complement Security Onion’s technology by capturing the network traffic (north-south & east-west) and providing all the data management required for a complete and effective security analysis in Security Onion. Using this data, security analysts can monitor networks in real-time and perform deep dive investigations, uncovering potential threats in your network.
The interface makes threat hunting easy to perform. Data sourced from your network, endpoints and applications are visualized directly in Security Onion, helping you proactively search for malicious activities. With the combination of data access and visualization, you are in complete control to implement a threat hunting gameplan tailored to your company and network environment.
Joint Solution
Visibility, performance and security. All are deeply important for the defense of your enterprise network. So what does the joint solution between Profitap and Security Onion Solutions look like in real life?
The solution can be split in two parts:
- Data access and intelligence
- Capture and analysis
Data Access and Intelligence
Reliable and accurate analysis stands or falls by the quality of the data that is captured. But you also need access in a way that does not impact the security of the network. It’s important that new appliances don’t add a backdoor for malicious practices on your network or, in case of a failure, cause network downtime.
Profitap’s network TAPs provide fail-safe access to the network and optimize the flow of traffic data by aggregating this into a centralized NPB. This way the Packet Broker is in an ideal position to perform advanced traffic management like deduplication and time stamping, forwarding only actionable flow data while keeping bandwidth usage to a minimum.
Capture and Analysis
With the help of Security Onion, you will be able to quickly analyze and pivot between all the different data types generated by Security Onion through a “single pane of glass.” This includes not only NIDS/HIDS alerts, but also metadata generated by Zeek and system logs collected via syslog or another agent transport. With one click, your analysts can pivot from alerts and metadata to full packet capture for relevant details.
The joint solution allows network analysts to effectively and quickly identify malicious activity in very high volume networks.
Main Benefits
- Fail-safe and real-time access to high performance networks with Network TAPs.
- Centralized management and traffic intelligence. Leverage advanced features such as deduplication, packet slicing, flow aware load balancing, advanced filtering and time stamping from a single GUI.
- Keep bandwidth usage low. Only actionable flow data is forwarded to the Security Onion sensor with Profitap Network Packet Brokers.
- Easily identify network security breaches and suspicious behavior through traditional detection and response as well as threat hunting.