Privacy law compliance with network analytics
THE CHALLENGE
- Compliance with new privacy laws require a new perspective on network visibility.
- Engineers have to “swim” through overwhelming amounts of data to find relevant info.
- Incident response is usually slow due to challenges of putting data together.
- Persistent Network Issues continue to elude even expensive solutions and platforms.
Cyberattacks on companies around the world have identified the need for more powerful security strategies, specifically an effective enterprise-level forensics and predictive security algorithms solution. Successful network security forensics and breach investigation includes post-event access to all the packets traversing the network.
Besides companies taking steps to maintain a secure and performant network, governments are also pushing the industry to safeguard critical company assets and ensure the privacy of the end-user.
Examples are regulations like GDPR and the latest and toughest regulation, the California Consumer Privacy Act of 2018 (CCPA), which becomes effective on January 1, 2020, is one of the most comprehensive and far-reaching new state rules. Even though the date for CCPA to become effective isn’t until January of 2020, certain provisions under the CCPA require organizations to provide consumers with information regarding the preceding 12-month period, and therefore activities to comply with the CCPA may well be necessary sooner than the effective date.
Businesses should strategize towards complying with both the imminent CCPA, but also, the growing tide of consumer privacy initiatives on the horizon. Companies need to think proactively about the data they collect, and how they want to use that data to further their business interests and stay within compliance of the particular national and state level regulatory environment. In so doing, businesses and companies should bear in mind that any data breach needs reconciliation and audit information that there were reasonable security procedures in place. A positive takeaway, businesses and companies that are able to demonstrate a documented history of taking affirmative steps to protect personal information will be wellsituated to defend any data breach consequences and can view data privacy and protection not as another compliance burden, but as an opportunity to build consumer trust and brand loyalty.
Quantea and Profitap have joined forces to provide businesses with a comprehensive network visibility and recording solution that helps you to stay in compliance with privacy laws, while also helping to keep the network performing at its best. Profitap’s network access hardware provides line rate traffic capture without dropping any packets and Quantea’s mission is to allow organizations to fully understand their networks. Capture, filter, store, replay and analyze network traffic packets in global networks. Allowing network investigation / analysis and hunting active defense to enable IT organizations and service providers to solve problems in today’s digital global marketplace.
JOINT SOLUTION
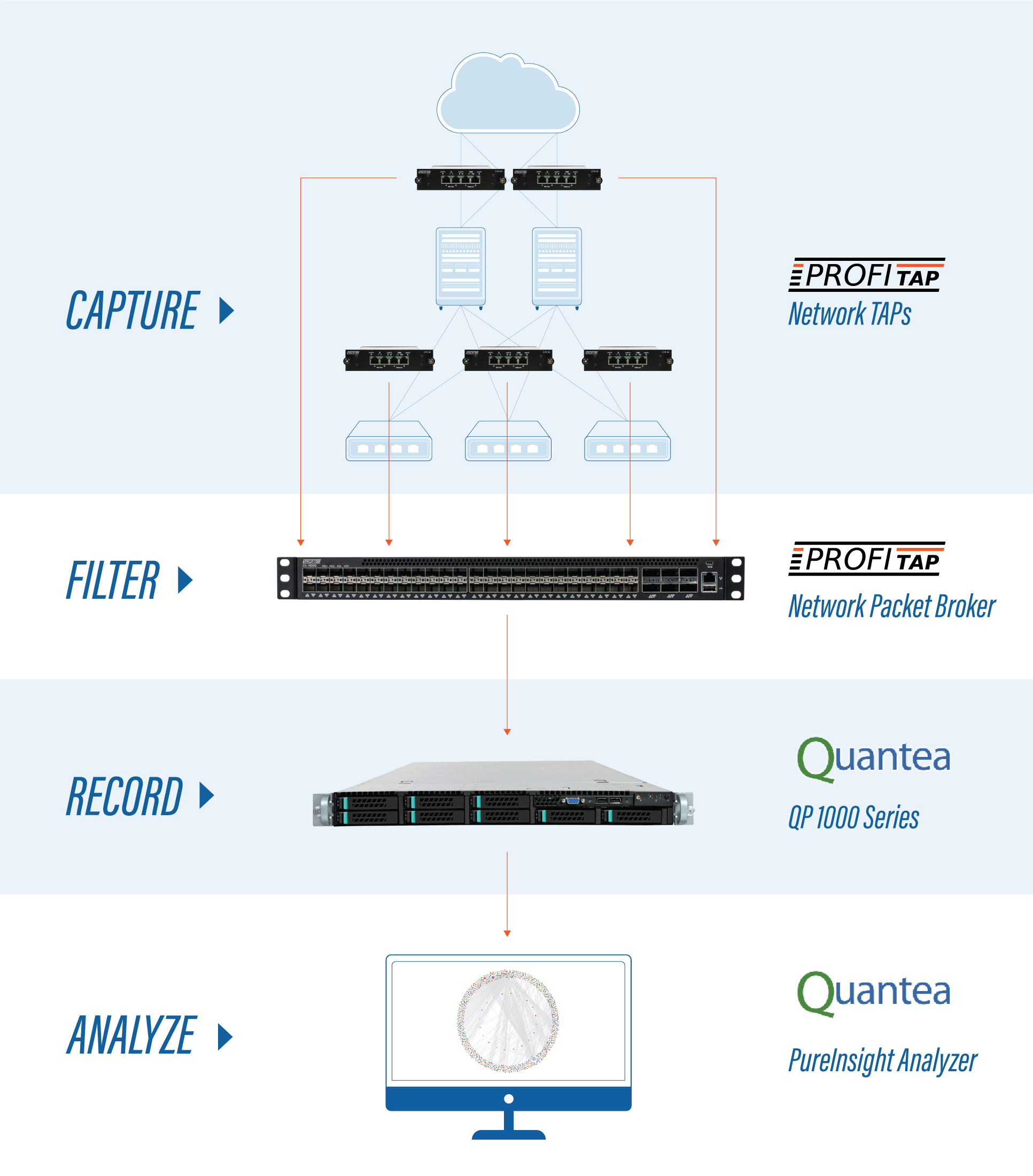
Capture with Profitap Network TAPs
The only way to be able to keep your network free of unwanted intrusions is to be able to see all that is happening on your critical network links. Network TAPs will copy 100% of the network traffic including error packets and layer 1 and layer 2 traffic.
Filter, Aggregate
Next the packets can be sent to a Network Packet Broker where they can be filtered and, if necessary, aggregated before they are sent to the QP Series appliance for storage.
Store Data on QP Series Appliances
Now that the traffic is safely in storage, it is available to the IT and Security teams from anywhere on the network for troubleshooting and fine-tuning your network critical links.
- QP for Cyber Security - The QP provides an effective way to quickly recall events in a network and provides a full record of a security incident – during, before and after.
- Network Optimization - At 100Gbps per single unit, the QP provides a reliable way to test and optimize your network using line rate replaying capabilities as well as software tools to drill down into what is slowing down your network.
- Quality of Services - The QP can be used to maintain records with full data integrity for compliance and for quality of services (QoS) verification and measurement.
Analyze with PureInsight
By using PureInsight, the user does not have to export the data to another tool to be able to analyze and drill down the network data into a relevant subset. View flow data quickly, being able to harness whole packet data while representing them in flow data is powerful.
Determine Gaps in Network Security
Quickly search for relevant information and PureInsight generates network mapping and usage graphs according to the search result packets. Determine gaps in network security by finding blacklisted nodes and unauthorized usage of ports/protocols.
View Network Top Talkers
PureInsight clears the noise of a complex network to useful information that can be quickly visualized. See the network top talkers with a few clicks and see whether it is a potential security or optimization issue.
Over 150 Protocols Supported
PureInsight supports a wide variety of protocols. Proprietary protocols can be added into PureInsight and can be integrated as a custom short-code for searching.
Purest Form of Network Data
PureInsight generates visualization from whole packet data. Display data by network flows and at the same time, retain all whole packet information. Analysis does not stop at the flow level, it begins at the flow level and all the way to the payload.